In this post I will explain you what Workload Identity Federation is and how to use it in the context of Azure.
If you do not understand what Workload Identities are, refer to this blog post about WIs.
What is Workload Identity Federation?
But…why should I use WIF? I mean, secrets do work.
Well, there are many reasons, for you to migrate to WIF.
First of all a software workload needs an identity to authenticate and access resources or for communication reasons.
So if you run these workloads on Azure, you can use managed identities (Read my blog post about managed identities here)
If you have a software workload, which runs outside of azure, you can’t use that.
So in the past you either had to use a secret or certificate to access these Resources protected by Entra ID.
That’s…insecure.
We all know that Passwords are not secret anymore today for our user, so why should they be for software workloads?
In addition, they need to be rotated regularly and if you don’t, you’ll risk service downtime, because of expired credentials.
WIF is here to configure a user-assigned managed identity or app registration in Entra ID to trust tokens from an external IdP (Identity Provider).
Once you created that trust, the external workload will be able to exchange trusted tokens from that external IdP for access token for the Entra ID.
The software then uses these access tokens to access the Resources under protection of Entra ID
How does it work?
Well you establish a trust relationship between the external IdP and Microsoft Entra ID.
The federated Identity Credential indicates, which token of the external IdP should be trusted.
The workflow for the exchange of external tokens for an access token, is standardized and with that, the same for all scenarios.
Following graphic of Microsoft shows the Workflow
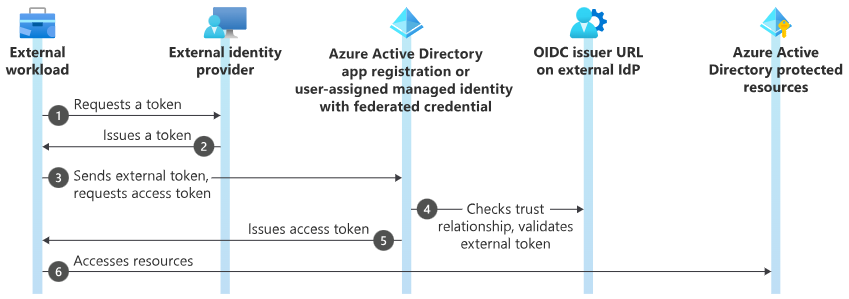
- In the first step, the external workload requests a token from the external IdP
- The token of the external IdP is issued to the workload
- With that token, the external workload sends an request for an access token
- Entra ID then checks the trust and validates the token
- If everything is valid, Entra ID issues the access token directly to the workload
- Then at the end, the workload can access the resources
Note: Microsoft as a IdP only stores the first 100 signing keys when they’re downloaded from the external IdP. When the external IdP publishes more than 100 keys, there might be error when working with WIF.
